Command Palette
Search for a command to run...
Just Now! The 3.15 Gala Named AI face-changing Fraud and Exposed the Black Market of motherboards. With a Cost of 2,000 Yuan, 20 Mobile Phones Can Be Released at the Same Time

On March 15, 1991, the "Friends of Consumers Special Evening Party" was broadcast on CCTV. Since that year, the "3.15 Evening Party" has become a regular program like the Spring Festival Gala, attracting the attention of hundreds of millions of Chinese people. Over the years, countless companies have been put on the "public opinion interrogation platform" on this night, including many well-known companies that are familiar to everyone.
As expected, this year's "3.15 Gala" still made people indignant and terrified...
In recent years, as emerging technologies have been more deeply integrated into people's lives, "technology for evil" has also quietly grown. Issues such as network security and data abuse have frequently appeared on the exposure list of the "3.15 Gala", and this year is no exception.
Tonight, the phenomena that were highlighted are:
* Motherboard for making navy
* Fire-resistant glass that is not fire-resistant
* Cut-price fire extinguishers
* The "bad meat" in preserved vegetable braised pork
* The magical Tinghua wine
* Information Security Lab: AI face-changing/voice-swapping fraud
* Dating and marriage platforms have complex schemes
* Disturbing BMW driveshaft
* Gift card scams in online lending
Motherboard black and gray industry chain: 2000 yuan cost, network trolls can change IP addresses
The evening party started with a talk about the issue of network information security, and the source is the old mobile phones that are most easily overlooked. Unscrupulous merchants collected the motherboards of old mobile phones and integrated them into "mainboard computers."
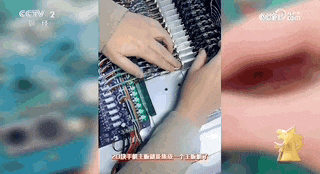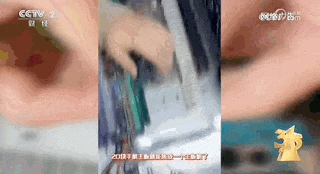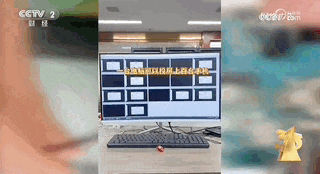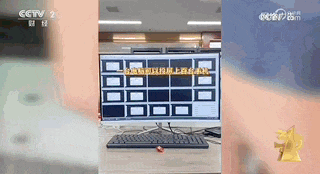
The reporter visited Yundou Technology, where the person in charge said that its product can install 20 motherboards into the same motherboard chassis, so one computer can control 20 mobile phones, equivalent to 20 accounts, with one IP for multiple devices or one device for one IP. The relevant manufacturer even said in its publicity that the motherboards they manufactured can be stacked up to form a network matrix of tens of thousands of mobile phones."Any activity that requires the user of the phone to participate can be controlled by the motherboard."
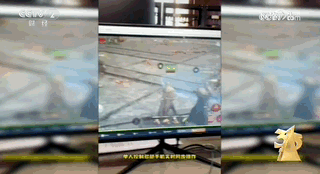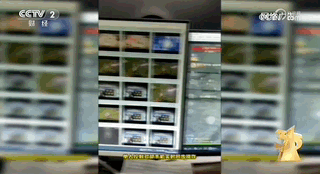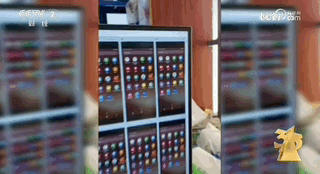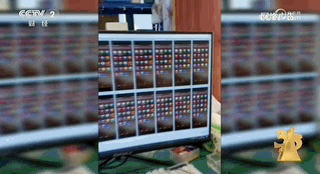
In addition, the person in charge of Yundou Technology introduced that one of the main functions of the motherboard computer is to acquire customers. The promotional videos about the motherboard computer on the Internet are operated by them using their own motherboard computers, and the IP addresses are spread across different regions such as Guangzhou and Shenzhen.
However, the illegal functions of the motherboard computer are far more than that. With the help of an insider, the reporter visited Yunjixia (Shenzhen) Technology Co., Ltd. and entered the company's workshop where motherboard computers are produced and modified. There is no sign outside the production workshop, but an illegal industry chain is running at high speed inside.
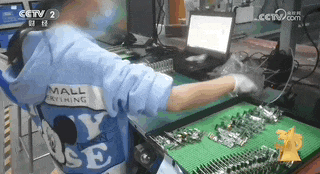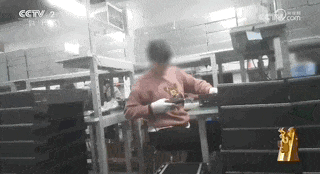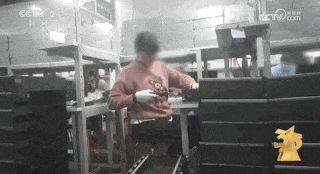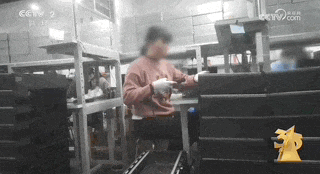
The reporter found on Yunjixia that the motherboards that make up the mainboard machine do not meet the network access standards of the Ministry of Industry and Information Technology. So where do these motherboards come from?
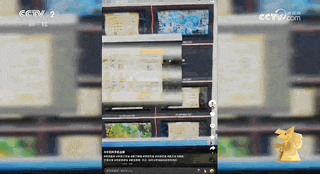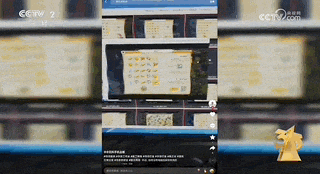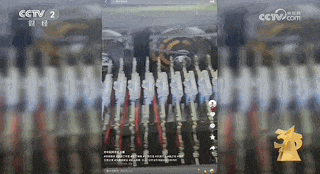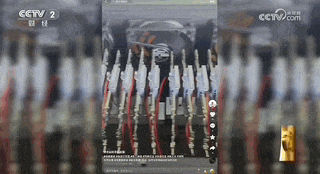
The relevant person in charge introduced that these motherboards were "collected" from the second-hand mobile phone market and are in very short supply.The cost of a second-hand mobile phone motherboard is 100-150 yuan, and the cost of a motherboard machine is about 2,000 yuan.
The relevant person in charge of Yunjixia introduced that the main board computers in the market are currently mainly used to increase traffic for live broadcast rooms, increase the number of promotional marketing articles, etc. At the reporter's insistence, the person in charge took the reporter to the main board computer room of a "small customer".Place insideIt has 50 motherboards and 1,000 motherboards built in, which is equivalent to 1,000 mobile phones.
In addition, when the reporter visited Yuncheng Future Technology Co., Ltd., he met Manager Liu, the promotion manager of an e-commerce platform who came to buy a motherboard. According to him,The company uses motherboards to spread information and promote customer acquisition."As long as I have your number, I can send it to strangers, and it will be a group link. There are still many consumers who take the bait with such a huge amount of information promotion."

What is even more shocking is that as the investigation deepened, the manufacturer relaxed its guard.The reporter was taken to a computer room with 10,000 motherboards, behind which were at least 200,000 accounts...

AI voice-changing face fraud, financial remittance of 1.86 million
In this year's "Information Security Lab", AI onomatopoeia/face-changing fraud was specifically exposed.
I believe many readers have a deep impression of the news that "the financial officer was defrauded by an AI face-changing video and remitted 1.86 million yuan." Ms. Zhang, a financial officer in Xi'an, Shaanxi, received a video call from her boss, asking her to transfer 1.86 million yuan to a designated account, and it was very urgent. Ms. Zhang felt that "the voice and image were the same as the real person", so she completed the transfer as required.

However, when she uploaded the electronic certificate to the company's internal financial group as required, the boss in the group saw the information and asked her why she transferred the money. At this point, Ms. Zhang realized that she had been defrauded. She immediately called the police and, with the assistance of the police, intercepted part of the transfer and successfully saved 1.56 million yuan.
Coincidentally, another Ms. Chen received a call, and the voice on the other end was her daughter's audio asking for help, produced using AI onomatopoeia technology.
Mr. Feng also received a cross-border video call from a friend, asking for help in purchasing a plane ticket.

In summary,All AI imitation/face-changing scams actually have a common loophole - short-term calls.
Because audio and video are almost always faked and recorded by fraudsters using AI in advance. In essence, using face-changing or voice synthesis to conduct real-time fraud in point-to-point video calls requires strong financial and technical support, including a large number of picture collections, professional algorithm/model training, high computing power reserves, etc., and it takes a long time of iteration to achieve realistic effects.
Professionals suggest that in real life,If you encounter a suspicious video call, you can ask the other party to touch their face or press their nose. These actions will cause data interference and the fake face will shake.
Final Thoughts
In recent years, the "AI content" of the 3.15 Gala has been getting higher and higher. The AI onomatopoeia/face-changing mentioned tonight is actually very common in people's daily lives, and the relevant technology has reached a certain level of maturity. For example, some algorithms can generate Stefanie Sun's version of "Hair Like Snow" and "Mohe Ballroom" based on Stefanie Sun's original audio, which can be said to be indistinguishable from the real thing.
On video platforms such as Tik Tok and Bilibili, more and more netizens have begun to use technologies such as AI-generated images and AI sound synthesis to carry out rich secondary creations. However, the platform will generally label the video "Content suspected to be AI-generated, beware of being deceived" based on its internal detection mechanism.
It is true that technological progress will always be an important engine for productivity change. At the same time, advanced technology may also be a breeding ground for black and gray industrial chains.
A person with ulterior motives can easily obtain a 10-second audio data through a harassing call from an AI customer service assistant, and then use the model to generate counterfeit audio and commit fraud. In addition, in real life, with the popularization of AI applications, consumers will inevitably use facial information for identity verification in public places and online platforms. The security of facial data in this process should also be taken seriously.
As consumers, we should also enhance our awareness of prevention and learn to exploit model loopholes for identification. Especially when it comes to monetary transactions, we must confirm with the person in person before transferring money.
I believe that as AI continues to do evil, the national level will introduce more detailed laws and regulations to provide stricter supervision and punishment. At the same time, on the technical level, we also look forward to more new anti-AI fraud results.