Command Palette
Search for a command to run...
Mango TV Used a Variety Show to Reveal the Dangers of Online Information Leakage

In the recently aired variety show "Celebrity Detective", several celebrities performed a case reasoning caused by information leakage through a fictional suspense story. As the evidence collection and analysis proceeded, the truth gradually surfaced, and at the same time, it also triggered deeper thinking.
Shocked!
Even variety shows have begun to involve information leaks, and the reality of the topics they explore is terrifying when you think about it carefully!
"Star Detective" is a reality show created by Hunan Satellite TV that brings the "script killing" game to the screen: all players (including the murderer) will perform their roles according to the established script, and finally deduce the hidden murderer of the suspense case.

In the latest episode of the variety show "Star Detective", a cyber security case of information leakage was reconstructed.
In this episode, in addition to the wonderful performances of each character, the subject matter is close to real life, making it an interesting and thought-provoking drama.
The death of a rich girl: six suspects
The story of this episode begins: Rich girl Zhen Xing (the victim) was found dead in a rented house. Because of a family inheritance dispute, her relationship with her stepmother became strained and she moved out to live on her own. The composition and background of the residents on the street where Zhen Xing lived were very complicated.
As more clues were uncovered, everyone from the victim's stepmother to her real estate agent and even the owners of the digital store and milk tea shop on the street became suspects.

Rong 3C (played by Yang Rong): Zhen Xing's (the victim's) neighbor, a digital product vendor who would steal customers' user information when repairing mobile phones and computer equipment.
He Fang (played by He Jiong): Zhen Xing’s (the victim’s) real estate agent, who has the key to Zhen Xing’s rental house and also found his online loan certificate among the clues.
Hou Houhe (played by Hou Minghao): The owner of a neighborhood milk tea shop, he collects a large amount of customer privacy information through QR codes in the store. He also has an unknown identity: the little prince of the black industry, who sells a large amount of customer privacy online.

Fairy Qi (played by Qi Wei): the stepmother of Zhen Xing (the victim), who shared the large inheritance of Zhen Xing's father with Zhen Xing and helped the underage Zhen Xing to keep it for safekeeping.
Sa Wei (played by Sa Beining): the owner of a neighborhood snack bar, Qi Xiannv’s ex-boyfriend, single, and emotionally unstable.
It seems that everyone has an unspeakable connection with the victim, and it seems that everyone has a motive for murder.
There is more than one murderer: a chain of evidence
As clues are discovered one by one, the truth gradually comes to light, but what is shocking is that it seems that everyone is involved and has become part of the crime.
This story involves multiple main lines, which are woven together through various clever relationships, and ultimately covers a variety of information security issues.
Clue 1: Information stolen during digital product repair
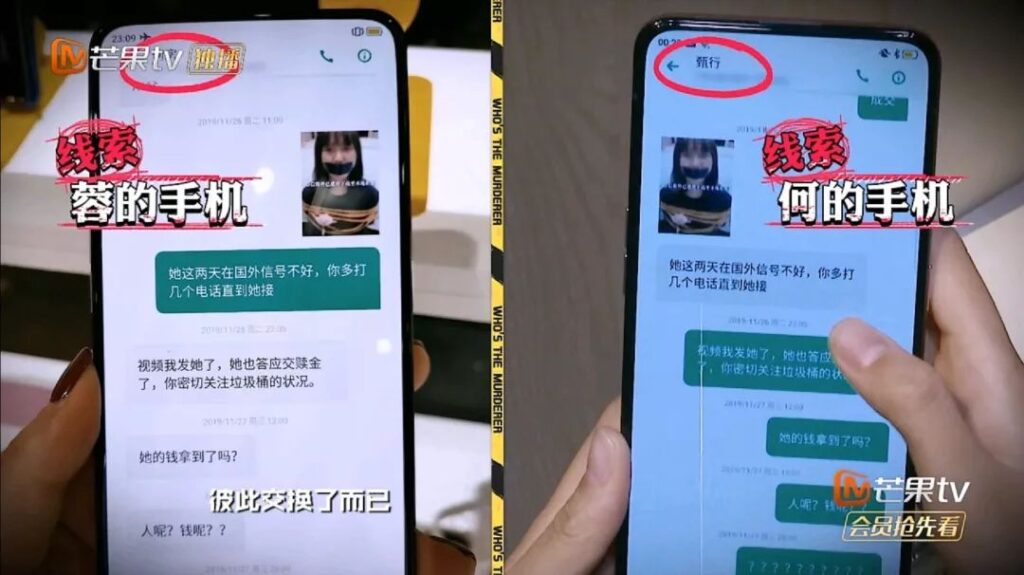
As a digital vendor, Rong 3C steals information and uses it maliciously when repairing customers' electronic products.
Nowadays, many people don’t remember their mobile phone numbers. Once someone changes their address book, or their nickname and image in WeChat, and disguises themselves as another person, many people may not be able to tell the difference.
Clue 2: Register as a member and submit various private information
In order to find the contact information of her stepdaughter, the stepmother had no choice but to turn to the black market prince for help, and did not hesitate to spend a large amount of money to buy her address and other information.
The information of the little prince of the black market was obtained from the membership information of his own milk tea shop. To register as a member of a milk tea shop, one needs to fill in very complicated personal information.
It is not uncommon to need to obtain a large number of user permissions when registering a member or app
Although the show is exaggerated, similar things do happen in the real world. When we register for an app, shop online, or join a membership, we inevitably need to provide some personal information.
Be sure to distinguish between: original APP and clone APP, fraudulent advertisements behind the health chicken soup in WeChat, e-commerce companies that collect excessive information, etc.
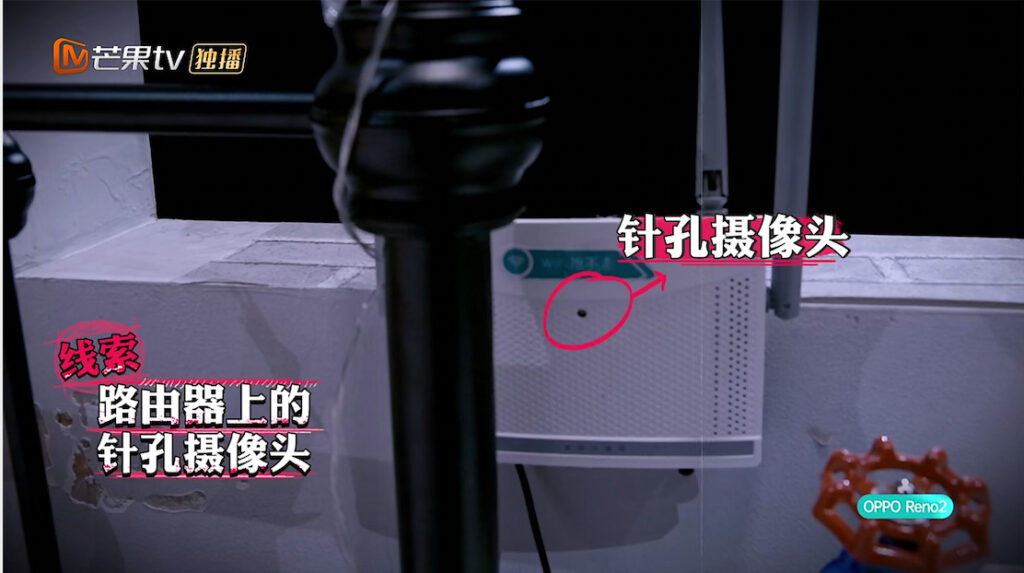
Clue 3: Cameras Everywhere
A pinhole camera was found on the router in the victim's home, facing the victim's wardrobe. Who installed the router has become a mystery.
In recent years, cases caused by various voyeuristic cameras have become common, some of which are installed in public places such as locker rooms, hotels, and schools. This is a clear violation of the law and crime. However, it is difficult to completely combat it because it is difficult to trace and investigate.
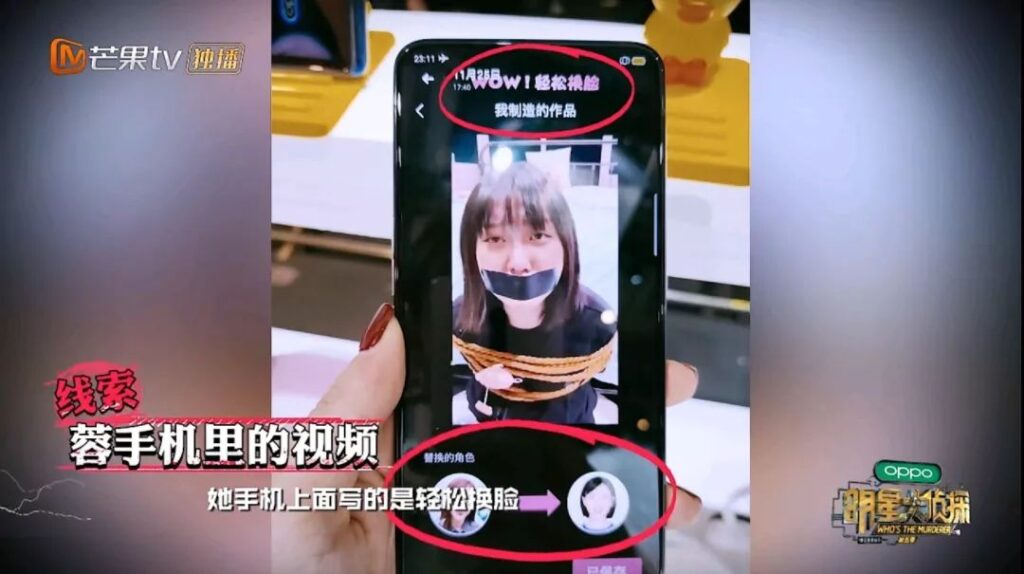
Clue 4: AI face-changing, forging someone else’s identity
A video with AI face-changing was found in the clue's mobile phone, which also showed that the mobile phone and AI face-changing were used to fabricate content.
In addition to posting fake social updates on mobile phones, Rong 3C sent a kidnapping video to his stepmother Qi Xiannv in order to extort one million yuan. This was actually his own actions combined with the content obtained by AI face-changing.
This seemingly bizarre move not only defrauded money, but also left neither the victim nor the payer unaware. Even more bizarre is that similar cases have occurred in reality.
For example, in March this year, a criminal gang used AI voice generation software to imitate and impersonate the CEO of a British energy company, deceiving the company's colleagues and partners, causing the company a loss of 220,000 euros (about 1.73 million yuan).
Clue 5: The deceased himself did not pay attention to protecting his personal information
What you post on social networking sites can reveal your information, especially when you are not aware of it. For example, when she posted a message online about needing a router, Jia Baiwan, who had ulterior motives, passed the equipment equipped with a camera to the relevant people, thus starting a planned surveillance.
If carelessness and negligence only target bad actors, active data privacy intrusion is a nightmare that is difficult to prevent.
If you don't watch it to the end, it's hard to guess what the truth is. Who is the murderer? Where did this confusing case come from?
We won't reveal any spoilers in the article, the truth is shocking and the method used is very bizarre, you can search and watch the full episode on the Internet.
Strengthen network security awareness, start now
The suspenseful story and the in-depth analysis of network security together create this episode of extremely high-quality content.
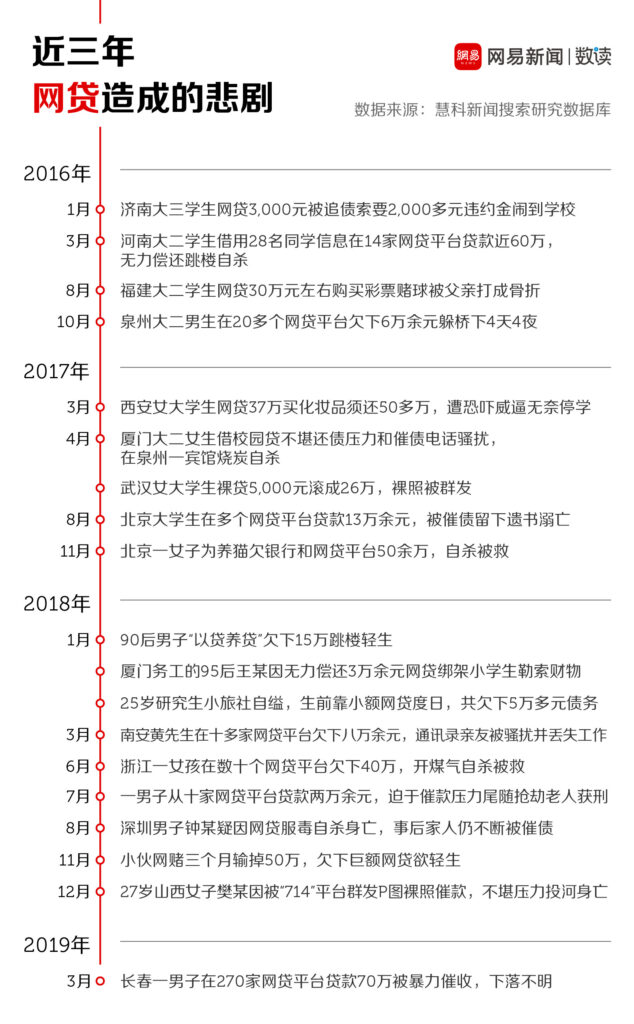
But the harm caused by the leakage of personal privacy information is the focus of our attention. There is a sentence in the program: "The most precious thing you have is yourself", but unfortunately, some young people under the trend of high consumption are using various online loans or even naked loans to meet their desires.

In reality, the development and convenience of the Internet has made the threshold for borrowing and lending lower, but once the personal information used for exchange is used maliciously, it will slide step by step into the abyss of darkness.
But in reality, neither the importance of security and privacy, nor the awareness and attention paid to these issues have been widely recognized and valued.
The data that carry our personal information may have inadvertently become a bargaining chip in the hands of businesses and black industries. Under the seemingly calm surface, there is a bomb that can explode at any time.
Protecting personal information privacy and expecting stronger regulation of technology may be what everyone wants to see. After all, even entertainment variety shows have begun to pay attention to these issues, so we can't let them down.
-- over--