Command Palette
Search for a command to run...
The Identity Has Been Replaced by Someone Else for 23 years. Who Gave the Impostor the Opportunity?

Recently, a story about a veteran named Wu Ruihua who had been working under someone else's name for 23 years has appeared in various reports. Behind the identity fraud, he was forced to fight against life. In fact, similar identity fraud incidents are also common and difficult to supervise in the process of receiving and distributing social security benefits. Fortunately, the use of technologies such as AI can greatly improve the situation of such fraud.
Recently, an incident of impersonation has attracted national attention.
After retiring from the army, Henan veteran Wu Ruihua originally got a job as a demobilized worker, but someone else used his identity. During the 23 years when he was impersonated, Wu Ruihua knew nothing about it and could only wander around, working, farming, and running small businesses to make a living.

The case is under investigation. The fake "Wu Ruihua" worked in the government of Yilu Town, Dancheng County, Zhoukou City, Henan Province. However, the "real Wu Ruihua", who was nearly 50 years old, missed the opportunity and went to a completely different fate.
This is not an isolated case of identity replacement. In reality, there are a large number of illegal acts such as impersonation, collecting on behalf of others, and falsely claiming benefits in order to obtain welfare benefits.
How to falsify personal identity?
In recent years, there have been many cases of impersonation being exposed.
In 2011, four years after graduating, Inner Mongolian girl Ma Qiaozhen discovered that a college entrance examination immigrant from Shandong named Xu Juanjuan had used her identity information to enter North China University in Shanxi from Inner Mongolia in 2006. After being impersonated, Ma Qiaozhen's academic qualifications from Inner Mongolia University of Finance and Economics could not be verified on the China Higher Education Student Information and Career Center.
In a case in Suzhou, Anhui in 2017, a woman named Miao Juan used all the identity information of others, including academic qualifications, photos, and ID cards, and worked as a teacher for 16 years;
These acts of impersonation and identity fraud exist in many links of social welfare benefits distribution. There is always a small group of opportunists who steal social resources by impersonating, defrauding, and falsifying.

Take pensions for example. According to statistics, from 2012 to 2016, a total of 760 million yuan in pension fraud was discovered nationwide, and 710 million yuan was recovered.
The reason why there are always people who want to steal benefits by impersonating others is that for a long time, our local civil affairs system was not sound enough and the supervision was not in place. There are always people who can achieve their goals by taking advantage of loopholes and using connections.
Common forms are:1. Forging or fabricating personal files, identity documents and other data; 2. Impersonating another person to obtain benefits by fraud; 3. Concealing the fact that one has lost the conditions for receiving benefits and continuing to obtain benefits by fraud or repeatedly.
In order to accurately distribute social security, a safe and effective confirmation system is urgently needed. In fact, many technologies are already being introduced into it, becoming a powerful tool to combat illegal activities.
Facial recognition: ensuring you are who you say you are
As facial recognition technology matures, AI begins to play a role in social security payment certification, ensuring that these funds are not fraudulently claimed.It is based on image analysis, calculates the visual feature information of the face, and uses the collected facial information to perform identity authentication and recognition.

Specifically, identity recognition is performed through biometrics and dynamic image comparison. The mature authentication systems on the market have a fast recognition speed. Generally, the facial model collection time of the system is only 10-15 seconds, and the identity verification time is only a few seconds.
By taking photos to model the data of the person to be authenticated, it is only necessary to collect the facial model information for the first time. After that, the authentication can be completed by simply connecting to the Internet. With the access of mobile client technology, the authentication can be completed directly using the mobile phone, safely and efficiently.
In addition, by collecting multiple facial information of a person and performing dynamic image comparison, it is possible to effectively prevent various fraudulent behaviors in authentication work. The accuracy rate in commonly used systems can reach more than 99%.
For example, using a smartphone APP, through the phone camera, with the help of the AI system, you can complete the pension qualification certification. And regular makeup, weight changes, skin aging, hairstyle changes and other factors will not affect the system's judgment.

Then, by connecting to the public security system's certificate information database and performing a 1:1 matching authentication with the user's current face photo, the recognition accuracy will be greatly improved. This authentication can effectively resist external attacks such as photos/short videos and determine that the recipient is a real person.
Voiceprint recognition: leaving no place for impersonation
Although facial recognition has been widely used and has greatly combated identity fraud, it is not absolutely safe. With the emergence of face-changing applications such as Deepfake and ZAO, there are still some security risks.
Faced with such situations,Another safer AI method - voiceprint recognition is also used in social security receipt certification.
Compared to the well-known facial recognition, voiceprint recognition has been slower to gain popularity. However, as a unique feature, voice can identify a person with a high accuracy rate.
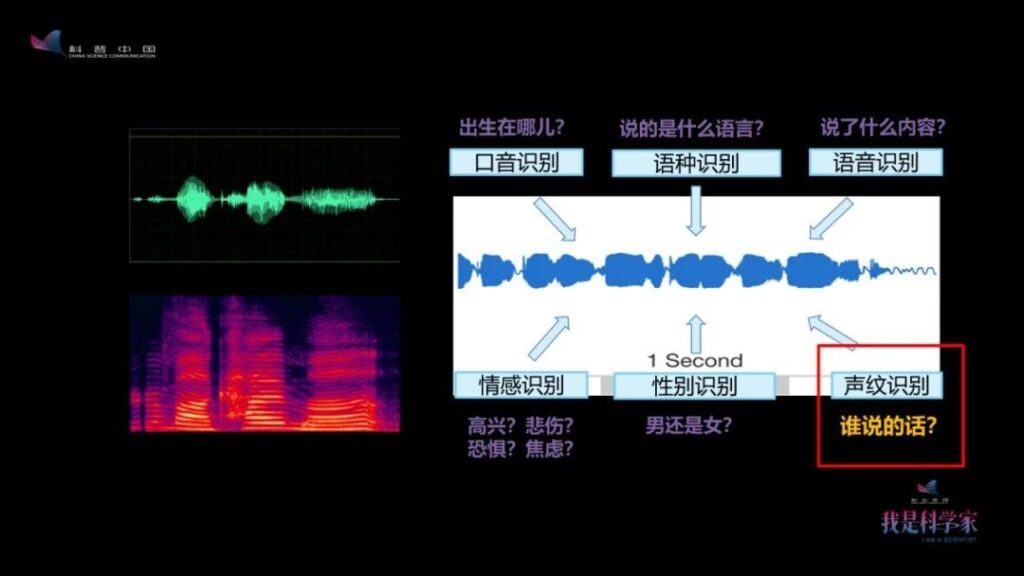
The principle behind this is that the voiceprint is determined by the physical structure of the human vocal system. The uniqueness of the human body structure determines that the voiceprint is also unique and can be used as a feature for individual identification.
Voiceprint recognition technology is very secure because the sound pattern is unique to the individual voice and is not as easy to copy as fingerprints and faces, so it is difficult to completely imitate.
Voiceprints include the speech features contained in speech that can characterize and identify the speaker, as well as the speech model established based on these features (parameters). Voiceprint recognition is the specific process of identifying the speaker corresponding to the speech based on the voiceprint features of the speech to be recognized.
Audio is collected through the mobile phone microphone. When applying for qualifications, the person can determine whether it is you by reading the randomly given numbers and comparing them with the voiceprint.

The whole process also involves basic voice recognition to determine whether the numbers are correct and avoid machine operation, but the most critical technology lies in voiceprint recognition, which is used to determine whether the person is alive and whether he is the real person.
By pre-installing the voiceprint identity authentication system and combining it with manual assistance, when the person cannot be present in person, remote identity confirmation can be performed by phone, thus improving the accuracy and security of the work of social security service agencies. This provides a good technical guarantee for the social security system to prevent fraudulent claims.
The "Voiceprint+" identity authentication cloud is being introduced in some regions. For example, some pilot areas such as Baotou City and Mudanjiang City have taken the lead in launching voiceprint authentication services for social security.
Technology brings fairness to people like Wu Ruihua
In many cases of identity substitution and resource fraud, the introduction of relevant AI technology can accurately determine whether the claimant is the real person, which will bring more fair and just results to the allocation of social security resources.
Of course, the implementation and popularization of technology also requires a certain amount of promotion and improvement. But fortunately, with the continuous advancement of technology, substitution and fraudulent claims are becoming more difficult.

I wish the world no longer needed to prove "I am me", and there will be no incidents of impersonation. This may be the warmest gift that technology brings us.
-- over--